(Works obviously for every other TLD as well)
As the new TLDs from Google already intend to be misused for shady phishing attacks and on the other side we can’t imagine any non-shady usage for those domains, we’ve decided to block those entirely.
We show you, how we’ve done that:
On the Windows DNS-Server (mostly the Domain Controller) we create a new Forward Lookup Zone:
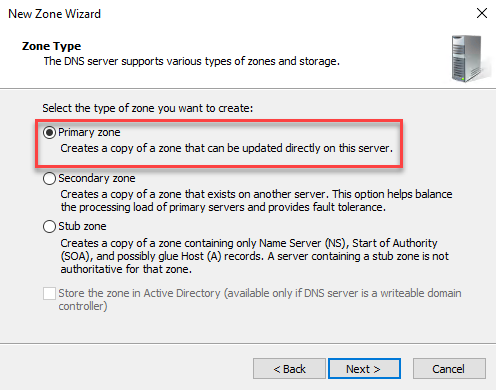
We select “Primary zone”:
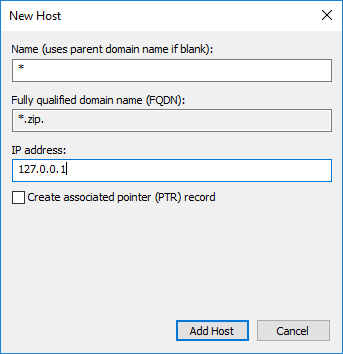
As “Zone name” we set the TLD to block, for example “zip” – Make sure to not add any points:
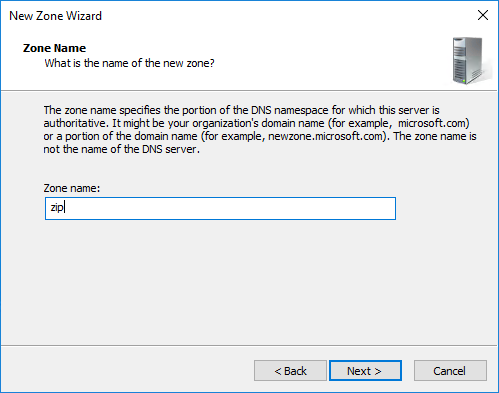
Next settings are fine already:
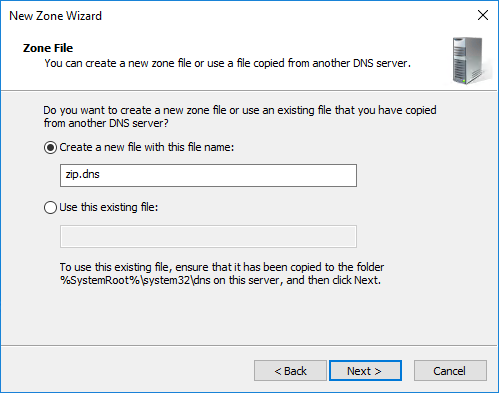
And this setting is fine by default, too:
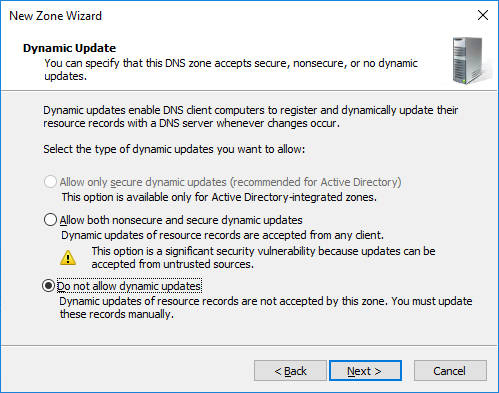
By clicking on “Finish”, we create the zone:
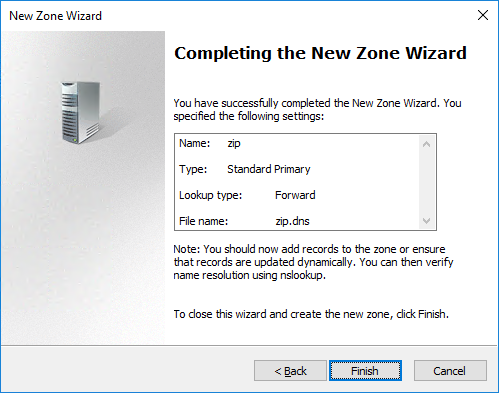
Now, it should look somehow like this in Forward Lookup Zones:
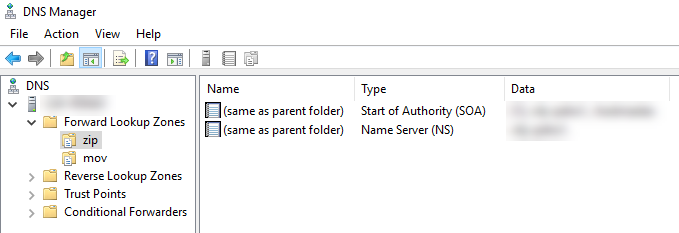
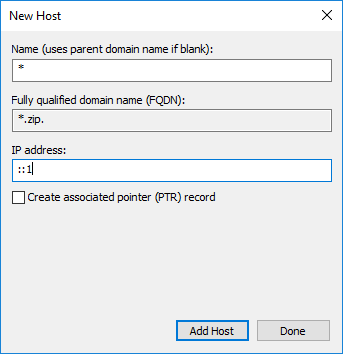
In each zone we now create an A- and an AAAA-Record with * as host und localhost as target:
… so it should look like this:
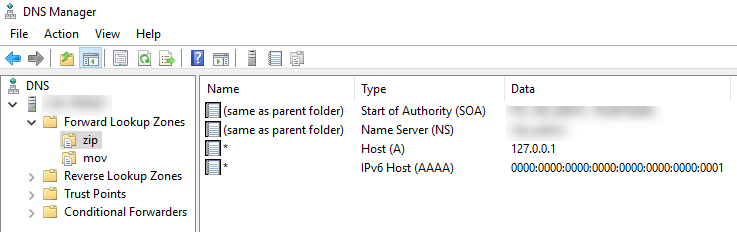
As soon as we created the records, every machine using this server as DNS-source should resolve names with those TLDs locally, so it’s only connecting to itself.
You could even go further to create a landing page on a webserver for those Domains – but this requires more configuration as you’d get a certificate warning when accessing with https://. So you would have to create a Wildcard-Cert on an internal CA as well.